Visier Under the Hood: Our Data Security Model
Find out how Visier’s data security model makes sure that the right users—and only the right users—have access to data and generated content.

A core pillar of Visier’s solution is our data security model. Note: when we say security, we’re not talking about cybersecurity. We’re talking about the access side of security—making sure sensitive data can only be accessed by the people within the company who need it, and who have the right permissions at the right time. In this post, we’ll get into why a security model is so important for people analytics software, what a security model actually is, and explain our approach.
The unique sensitivity of people data
HR data is probably the most sensitive data set in a company, second only to financial data. HR data is incredibly personal (compensation, performance reviews, personal details, etc.) and contains personally identifiable information (PII). Compensation is also sensitive company data. The way a company pays its people is a proprietary part of its business strategy.
Within HR data, there are various levels of sensitivity:
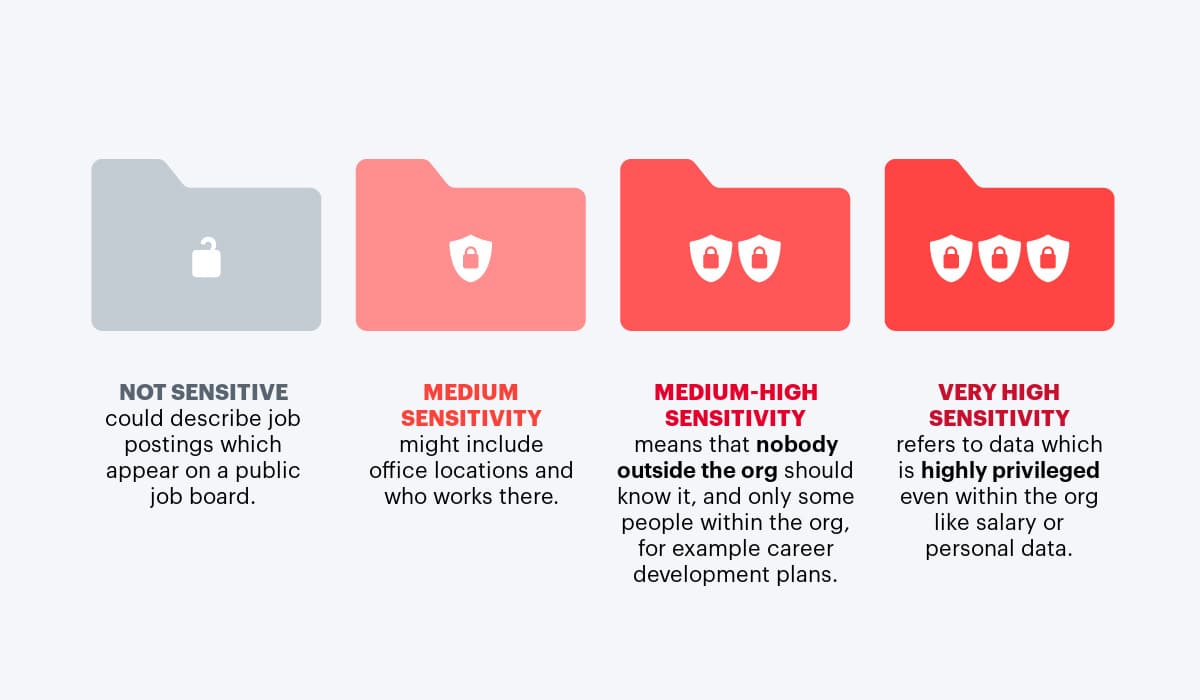
What makes HR data unique is its complexity. Whereas financial data is pretty much all sensitive, HR data has a spectrum and has to be handled delicately.
What is a security model?
A security model is the way security considerations are built into the design of the software. Think of a hotel’s keycard system. Hotel guests only get access to their own room and common spaces like the pool and the lobby. Housekeeping staff get access to all the rooms. Administrators govern this access.
Just as the hotel building design allows access control, Visier’s architecture handles sensitive HR data while being flexible enough to handle the wide variety of roles and permission levels present in an enterprise with tens of thousands of employees.
Security access layers
An Excel spreadsheet offers a good analogy to understand the various layers of our security model. Imagine rows and columns. Each column represents a different type of data. For example, if you were looking at employee data, the columns would be attributes of the employee such as age, gender, department, or length of service. Each row is an instance of that data. In the example above, each row would be an individual employee.
Now, let’s think about access. People need different levels of access depending on their role. Some users may require access to an entire set of records. For example, the CHRO will typically receive blanket access to all people data. Other users might need access to a subset of rows, subset of columns, or a subset of rows AND columns.
For example, a people leader needs to see all data about the people on their team, but no data from those on other teams. Or an internal events manager may need to see everyone’s birthday, but nothing else. Other users may need access to all data, but only at an aggregate level of detail without any personal details. An example of this is an HR staffer who needs to see the results of an employee engagement survey, but not the individual survey responses of any individuals.
A large, complex enterprise may need hundreds of combinations of access. The security model needs to be configurable enough to give everyone just the right level of access they need, but no more.
Managing content security
Once Visier customers bring HR data that they pipe into Visier, we do a lot of interesting things with it! Content is what we’ve built in Visier on top of the data. It’s what lets our customers get insights from the data. Here’s a simple example of the difference between content and data: an employee’s date of birth is a piece of data. But from that, we can calculate the content, such as their age, their age range, their retirement eligibility, and the generation they belong to. Content is data in context.
Content is also sensitive information, and another layer in our security model. A user might have access to one piece of content but not another, even if based on the same piece of data. For example, a DEI office might need to know an employee is Gen Z but not know her exact age. Visier handles all this complexity for our customers. We’ve built in complete configurability on the data side (what information we’re granting access to) and the content side (how the information is presented in context). The administrative users have complete and granular control over this.
Visier’s unique security model
Each of our customers and partners has unique needs for how to parcel out access to their people data, which is why we’ve designed our security model to support virtually any use case. Another big part of what makes our security model unique is the way that we can define access levels for various groups of users, rather than just individual users. A large enterprise organization often has dozens or hundreds of employees with similar access levels. Configuring each one manually takes too much time. This is why Visier has “user groups.”
User groups and access
Our security model allows for two logic-based approaches to define the access level for a user or a user group: Standard and dynamic logic-based access.
Logic-Based Access (Standard)
In Visier, you can define logic for which populations you want to have a certain level of access. For example, you might want to create a rule that says that a specific UK-based HRBP has access to certain information about employees based in the UK. But what about if an employee moves to the UK from another region? Visier’s security model can handle that. As soon as the employee’s region is changed in the HRIS system, Visier will update their level of access.
Logic-Based Access (Dynamic)
Dynamic logic is a very scalable method that comes in very handy in large organizations. Here, Visier administrators can define access levels based on the user’s position in the organizational hierarchy. For example, you might want to define a rule that says that all branch managers can see their direct reports’ data, but nothing else. Instead of having to manually assign each branch manager’s access, Visier will automatically configure the right access for each of them. As people join and quit the branch managers’ teams, Visier automatically updates the access.
Flexible security model
We take the flexibility of our security model even further. If you’re a Visier admin setting up access levels for users, you can set up logic that is based on more than one attribute of your employee data. For example, you can set up a rule that says that a certain HR role can see the salaries of people in one region and a specific department. For example, maybe a certain manager can only see performance data for one department, but can also see the exit rate for the entire company.
You could even combine and/or statements in your rules: perhaps a certain HRBP can only see compensation for one pay grade and one department, but can also see career development goals for another location. The deep flexibility of Visier’s security model means that each user gets exactly what they need, even in very specific areas of the business.
With our approach, large organizations can empower anyone in the business with access to exactly the right people data (and nothing more), without the need to build and maintain custom dashboards for each set of users.
The right access for all users
Imagine having to build dashboards in a business intelligence tool for a junior HR support person in a small business unit in an emerging market. Their needs might not be high-priority enough to justify building, deploying and servicing dedicated dashboards just for them. But with Visier, it’s just a matter of configuring access once, and that’s it. This approach makes it possible to distribute people data insights where they’re needed across the entire business, helping to close the people impact gap.
Our security model is one of the main reasons why our enterprise customers and partners choose and trust us. Easily providing the right people—and only the right people—access to employee data and content is a core competency and a big differentiator.
This blog only touches the surface of this highly technical topic. If you’d like to learn more, get in touch to schedule a demo or start a 30-day free trial of Visier People®, which comes with sample data and complimentary access to email and community support.
On the Outsmart blog, we write about people analytics and HR technology topics like how bad data can’t stop good people analytics, the benefits of augmented analytics, and everything you need to know about HR data sources and HR data connectors. We also report on trending topics like artificial intelligence, using generative AI in HR, and how skills are rapidly evolving, and advise on people data best practices like how to ingest people data and business data, how to turn source data into insights, and reports vs. analytics. But if you really want to know the bread and butter of Visier, read our post about the benefits of people analytics.


